Security risk assessment is an essential component of cyber security operations since it protects the company from intrusions, attackers, and cybercriminals. It’s not always clear what we’ll get regarding security risk evaluations. Providers employ meaningless and abused phrases, and several ambiguous or imprecise meanings accessible. Security risk assessment comprises detecting and managing security threats that affect the firm using IT infrastructure services. A security risk assessment identifies, assesses, and implements critical application security controls. Its purpose is to evaluate the company’s security posture and determine whether or not the company conforms to compliance standards and industry guidelines.
Table of Contents
How does it work?
The extent of risk assessment models is influenced by factors like size, growth rate, available resources, and portfolio of assets. When a company’s money or time is limited, it can do a generic assessment. On the other hand, generalized assessments may not always give detailed mappings between assets, associated threats, identified risks, effects, and mitigation mechanisms.
A more in-depth assessment is required if the generalized assessment results do not show a strong enough association between these areas.
Demanded by:
It is required for several compliance standards like:
- Payment Card Industry Data Security Standards (PCI-DSS)
According to PCI DSS requirement 12.2, any organization that processes or handles payment cards must implement a risk assessment approach done at least yearly and anytime there are significant changes in the environment.
Critical assets, threats, vulnerabilities, and the impact on the cardholder data environment must all be identified throughout the risk assessment process. The risk assessment should result in a formal, documented risk analysis.
- International Organization for Standardization (ISO)
To comply with SOX Section 404, these firms must do a top-down risk assessment (TDRA). The TDRA’s goal is to establish the efficacy of a firm’s internal controls, and its execution, depending on the organization’s size, may necessitate the use of an external auditor.
- Health Insurance Portability and Accountability Act (HIPAA)
All covered companies and business associates remain required by the Health Insurance Portability and Accountability Act (HIPAA) to conduct security risk assessments to identify risks and prevent data breaches. If a data breach remain discovered, an assessment must remain conducted to establish the level of danger posed to individuals and to disseminate this information appropriately.
What is the significance of security risk assessment?
A security risk assessment should leave nothing to chance since it is one of the most critical actions in cyber security. Untrained hands’ manual mistakes and omissions may be expensive and damaging to your company’s reputation. There are various risk assessment misconceptions, many of which remain used to excuse not obtaining one.
Some argue that these investigations are overly time-consuming, expose information that people already know, or are unnecessary if firms already have “great security.” With the assistance of IT infrastructure support, conducting cybersecurity risk assessments assists in avoiding possible security risks to a company. Security officers must understand the linkages between security and physical, social, and political threats to defend the company.
-
Risk assessments can help protect from security breaches.
One of the most important reasons businesses assess their risk is to protect themselves from costly and disruptive breaches. Risk treatments can help protect the company from cyberattacks and improve the security of confidential data. Security officers should understand the relationships between security components, including threats, vulnerabilities, and risks, to secure the organization from physical, socio-economic, and environmental threats. It further helps an organization to:
-
Risk assessments provide data that can be used to prioritize security enhancements.
Making dozens of changes to your cybersecurity at once is challenging (and sometimes impossible) for technological, operational, and financial reasons. A risk assessment eliminates the need for you to do so. The assessment will assist in justifying which areas require improved security, prioritizing which vital concerns require immediate attention, and determining which risks organizations are ready to accept.
-
Risk evaluations aid in the direction of your security investment.
It may be not easy to understand the benefit of investing thousands of dollars in improving its cybersecurity program. A complete risk analysis will outline which vulnerabilities remain prioritized and why and the impact each may have on your business if ignored. When the stakeholders and investors see how much not making the adjustments could cost them, they may be more willing to allocate funds to risk management.
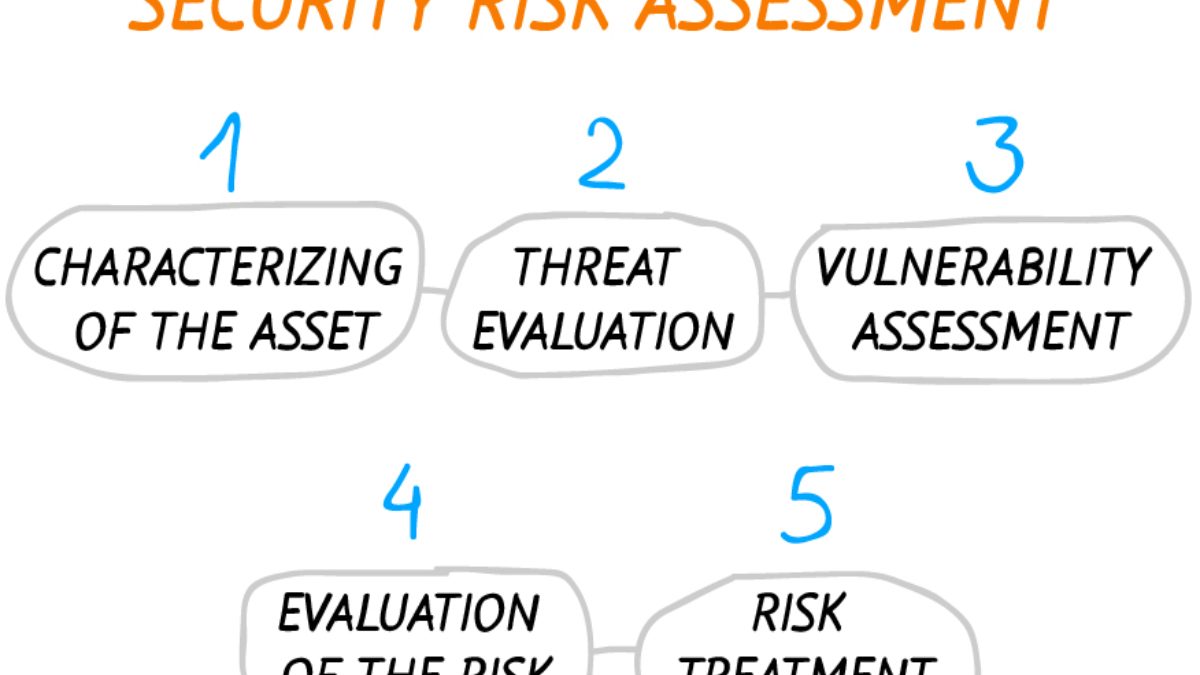
Steps in Security Risk Assessment:
- Identity: The security risk assessments enable the organization to identify the organization’s essential technology assets and the sensitive data generated. Stored, or transmitted by those devices. This information is critical for building risk management systems suited to the company’s specific requirements.
- Review: Examine existing security policies, standards, guidelines. And processes, as well as identify sensitive data created, held, or transferred by technological infrastructure assets.
- Assess: Implement a strategy for assessing the security risks identified for critical assets. Following a thorough review and assessment, determine how to effectively and efficiently deploy time and resources to risk reduction. The assessment technique or approach must investigate the connection between assets, threats, vulnerabilities, and mitigating controls.
- Mitigate: Examine and analyze assessment reports to determine how to devote time and resources to risk reduction. Implement technical measures to address identified vulnerabilities and reduce security risk. Assign corrective actions and suggestions to appropriate individuals to enforce security measures for each risk.
- Prevent: Conduct regular security assessments, watch for changes, and share risk assessment results with an authorized individual. Reduce the likelihood of threats and vulnerabilities occurring by streamlining reporting processes.
Who should perform?
For corporate operations, most companies require some amount of personally identifiable information (PII) or personal health information (PHI). If the firm has a dedicated IT staff, assign them to create a detailed grasp of the organization’s data infrastructure. And collaborate with team members who understand how information travels throughout the organization. If the company is small and does not have its own IT department. It may need to outsource the process to a professional risk assessment firm.