Online security within organisations should be the top-most priority to protect sensitive data. Due to this, cybersecurity is becoming essential for businesses of all sizes. As the scope of threats crosses the threshold limit and continues to rise at a fast pace, new opportunities are blooming up for qualified data professionals in the cybersecurity sector.
Check out vpn providers like diebestenvpn and getmoreprivacy
It involves securing sensitive data, computer systems, networks, and software applications from vicious cyber-attacks.
Cyber attacks tamper with systems and data stored within them, exploit resources, get unauthorized access to the system, and access sensitive information. It also involves agitating the normal functioning of the business and its processes. Personification is on top-notch cyber-attack activity. This is where cyber security comes into effect.
Table of Contents
What is the need of the hour?
Cyber Security has become a necessary factor for any business in the 21st century. As rift after rift hits the headlines, it can be identified that organisations need more professionals focusing on cybersecurity. Surely, it is a growth area that will remain critical for any business. To ensure eventually decrement in cyberattacks, HONEYPOT has been introduced.
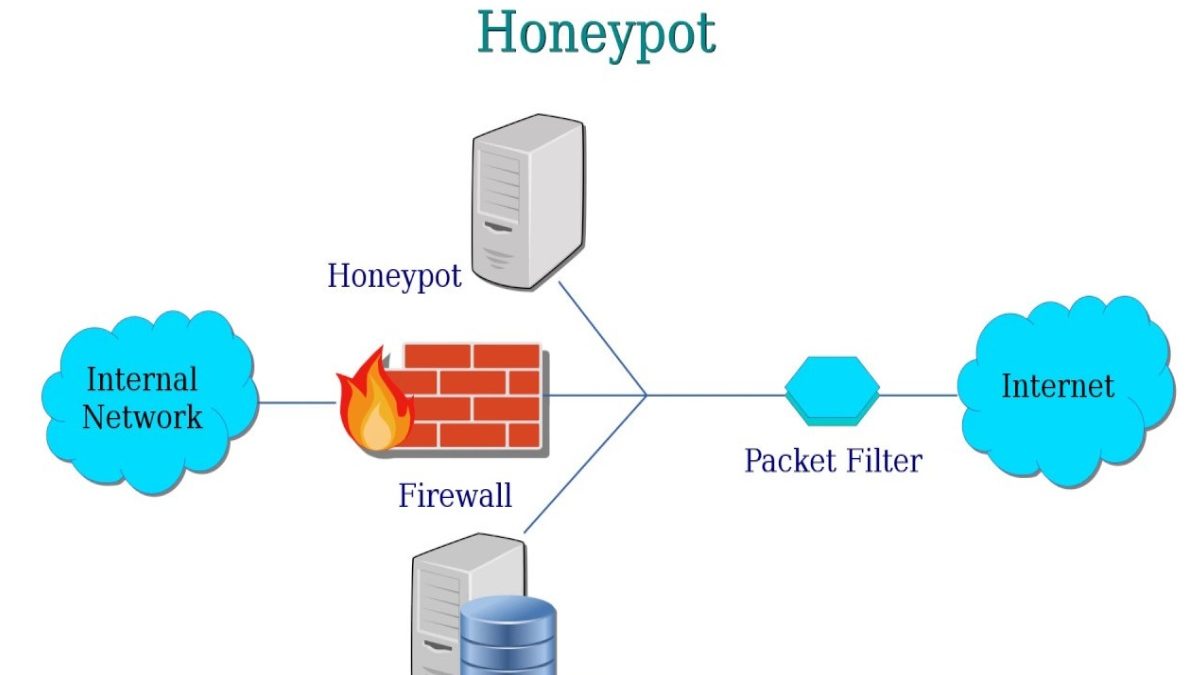
What is a honeypot in Cyber Security?
Honeypots attract cyber attackers by creating intentional security amenability.
A honeypot isn’t built to deal with a significant problem. Instead, it’s an important tool that helps you understand already visible threats to the business and figure out the new threats. Honeypots make cybersecurity more focused and intelligent to deal with security threats.
Types of honeypots
Honeypots protect the cyberattacks with various threat types that are addressed. They are very different from each other, such as:
- Email Traps put counterfeit mail ids in a secure place with an automatic address generator and find them. Messages sent by default get halted, and the relevance of the Internet Protocol address which an empty list can join a sender.
- A decoy honeypot database is to remain organized to check software amenability and detect attacks exploiting system which is not secure to architecture or major harm to an organization.
- A worm honeypot imitates various application programming interfaces to attract trojan attacks. The trojan features can remain evaluated to create anti-trojan system shut amenability in the Application Programming Interfaces.
- A webbed honeypot is expected to trap web crawlers (‘spiders’) by building networking pages and helping the cyberattackers crawl through the system. Observing the attackers may assist one know how the malicious activities can remain blocked and hurdled to avoid interfering more in the data delivery.
By enabling Honeypot in the security system it detects the stages of threat the organization has on the information and multiple apps the hackers wanted to take place.
Honeypots Diversified
Low- interacted honeypots use middling effects and gather basic data about the stages of threat in the organization. They are accessible and speedily created, just with IP protocols or some network services. Honeypot never stays long to bind the hacker instilling for cyber attacks.
High- interacted honeypots target to attack the hackers by involving them more in the activity, giving a lot of data and information and goals and the amenability they will exploit. The hackers remain engaged much longer so that the researchers may find them. The researchers get through the uses of tools used by hackers.
A mixture of honeypots requires the organization to cleanse the essential data and threats that come in the way. Primary communication is necessary to deal with the upcoming and existing threats to prevent the organization from exploitation.
Benefits of using Honeypot in Cyber Security
- Honeypots are valuable to expose susceptibility in computer systems. It detects threats from IoT activities. It also recommends areas and methods that the security can remain enhanced.
- Any malicious activity can remain detected using this mechanism. It makes it easier to verify the patterns, like the same IP addresses used to drag the networking stretch. In contrast, any suspicious prints of a barrage that are accessible drop in the buzz when one aims to increase levels of reasonable traffic on the major network.
- The most crucial gain of utilizing honeypot custody is suspicious addresses are the only ones that depict cyber attacks.
- They aren’t accustomed to hardware devices; it’s easy to construct a honeypot utilizing oldish computers that are no longer in benefit. As for software, numerous completed honeypots are available online, further decreasing the necessary in-house efforts to get a honeypot running.
- Honeypots have a low false-positive rate.
- Honeypots give dependable intelligence about how threats are emerging. They transfer data about attack vectors, exploits, and malware, and, in the case of email traps, about spammers and phishing attacks. Hackers frequently change their intrusion techniques, and so honeypot helps to detects newly emerging threats and intrusions. Better use of honeypots helps to abolish blind spots.
- Honeypots are better training tools for technical security staff. It is a controlled and safe environment for letting attackers work and evaluating various types of threats. Honeypot security doesn’t deviate staff from real and major attacks.
- Honeypots can also detect internal threats. It gives you equivalent acceptable data about internal threats and views amenability in areas that exploit the system.
The dangers of Honeypot in Cyber Security
- Honeypot cannot see all the activity, which is suspicious, but the only one allocated to it to check. One cannot wholly rely on honeypots to enable more prestigious IT security systems in their organization.
- However, if an attacker detects a honeypot, they will attack other systems that do not have a honeypot leaving it unaffected.
- If a honeypot gets detected, the attackers might fool it and distract attention from an actual exploit area being aimed against production systems. They can also deliver and admit wrong data to the honeypot.
- Honeypots can never replace any other security IT places. One cannot completely depend on it.
- A honeypot should provide information to arrange the major cybersecurity efforts, but it can’t reinstate the key cybersecurity. Kaspersky uses its honeypots to detect internet threats, and therefore it is not binding to add more security. Due to this, understanding Honeypot by getting trained with an advanced cyber security program is crucial.
But the benefits are of more weight than the risks. Hackers may always find new ways to intrude into the system, but honeypots provide it with a good guard.
The Bottom Line
Honeypots are cost-effective, due to which many organisations can incorporate them to increase security as they test for malicious activity. The team needs to take proper measures while depicting threats, and for that, it is fruitful for the organization not to bind on other IT security systems. Honeypots should not be the whole threat detection approach, but they should remain the ones to depict major areas which remain bombarded with hackers.
The question “what is a honey pot in Cyber Security?” has remained answered in this article. That’s why they’re essential and significant tools for organization benefits, and researchers key to lessening the workload. Various honeypot tools have different features and are basic applications which anyone wants to secure. Honeypots are an open-source tool that protects the organization to deal with all malicious activities. Therefore, many institutions are providing cyber security training that can aid organisations towards stable business functioning.
Therefore, for organisations that are wanting to take an initiative approach towards enhancing their defenses, honeypots can provide numerous benefits.
References:
https://www.kaspersky.co.in/
https://resources.infosecinstitute.com/topic/what-is-a-honey-pot/